A
cryptocurrency is a digital asset designed to work as a medium of exchange that uses strong cryptography to secure financial transactions, control the creation of additional units, and verify the transfer of assets.
Cryptocurrencies are a kind of alternative currency and digital currency (of which virtual currency is a subset).
Cryptocurrencies use decentralized control as opposed to centralized digital currency and central banking systems.
The decentralized control of each cryptocurrency works through distributed ledger technology, typically a blockchain, that serves as a public financial transaction database.
Bitcoin, first released as open-source software in 2009, is generally considered the first decentralized cryptocurrency. Since the release of bitcoin, over 4,000 altcoins (alternative variants of bitcoin, or other cryptocurrencies) have been created.
The first cryptocurrencies
The first decentralized cryptocurrency, bitcoin, was created in 2009 by pseudonymous developer Satoshi Nakamoto. It used SHA-256, a cryptographic hash function, as its proof-of-work scheme. In April 2011, Namecoin was created as an attempt at forming a decentralized DNS, which would make internet censorship very difficult. Soon after, in October 2011, Litecoin was released. It was the first successful cryptocurrency to use scrypt as its hash function instead of SHA-256. Another notable cryptocurrency, Peercoin was the first to use a proof-of-work/proof-of-stake hybrid. IOTA was the first cryptocurrency not based on a blockchain, using the Tangle instead.
On 6 August 2014, the UK announced its Treasury had been commissioned to do a study of cryptocurrencies, and what role, if any, they can play in the UK economy. The study was also to report on whether regulation should be considered.
How is a cryptocurrency defined?
According to Jan Lansky, a cryptocurrency is a system that meets six conditions:
- The system does not require a central authority, its state is maintained through distributed consensus.
- The system keeps an overview of cryptocurrency units and their ownership.
- The system defines whether new cryptocurrency units can be created. If new cryptocurrency units can be created, the system defines the circumstances of their origin and how to determine the ownership of these new units.
- Ownership of cryptocurrency units can be proved exclusively cryptographically.
- The system allows transactions to be performed in which ownership of the cryptographic units is changed. A transaction statement can only be issued by an entity proving the current ownership of these units.
- If two different instructions for changing the ownership of the same cryptographic units are simultaneously entered, the system performs at most one of them.
In March 2018, the word ‘cryptocurrency’ was added to the Merriam-Webster Dictionary.
What are an altcoin and a crypto token?
Stephanie Yang of The Wall Street Journal defined altcoins as “alternative digital currencies,” while Paul Vigna, also of The Wall Street Journal, described altcoins as alternative versions of bitcoin. Aaron Hankins of the MarketWatch refers to any cryptocurrencies other than bitcoin as altcoins.
A blockchain account can provide functions other than making payments, for example in decentralized applications or smart contracts. In this case, the units or coins are sometimes referred to as crypto tokens.

How are cryptocurrencies designed?
Decentralized cryptocurrency is produced by the entire cryptocurrency system collectively, at a rate which is defined when the system is created and which is publicly known.
In centralized banking and economic systems such as the Federal Reserve System, corporate boards or governments control the supply of currency by printing units of fiat money or demanding additions to digital banking ledgers.
In the case of decentralized cryptocurrency, companies or governments cannot produce new units and have not so far provided backing for other firms, banks or corporate entities which hold asset value measured in it.
The underlying technical system upon which decentralized cryptocurrencies are based was created by the group or individual known as Satoshi Nakamoto.
As of May 2018, over 1,800 cryptocurrency specifications existed.
Within a cryptocurrency system, the safety, integrity and balance of ledgers are maintained by a community of mutually distrustful parties referred to as miners: who use their computers to help validate and timestamp transactions, adding them to the ledger in accordance with a particular timestamping scheme.
Read more about the Distributed Ledger Technology(DLT).
Most cryptocurrencies are designed to gradually decrease the production of that currency, placing a cap on the total amount of that currency that will ever be in circulation. Compared with ordinary currencies held by financial institutions or kept as cash on hand, cryptocurrencies can be more difficult for seizure by law enforcement. This difficulty is derived from leveraging cryptographic technologies.

Blockchain and cryptocurrency
The validity of each cryptocurrency’s coins is provided by a blockchain. A blockchain is a continuously growing list of records, called blocks, which are linked and secured using cryptography.
Each block typically contains a hash pointer as a link to a previous block, a timestamp and transaction data. By design, blockchains are inherently resistant to modification of the data. It is “an open, distributed ledger that can record transactions between two parties efficiently and in a verifiable and permanent way”.
For use as a distributed ledger, a blockchain is typically managed by a peer-to-peer network collectively adhering to a protocol for validating new blocks. Once recorded, the data in any given block cannot be altered retroactively without the alteration of all subsequent blocks, which requires collusion of the network majority.
Blockchains are secure by design and are an example of a distributed computing system with high Byzantine fault tolerance. Decentralized consensus has therefore been achieved with a blockchain. Blockchains solve the double-spending problem without the need of a trusted authority or central server, assuming no 51% attack (that has worked against several cryptocurrencies).
Read more on What is Bitcoin and how does Bitcoin work?
Blockchain and Timestamping
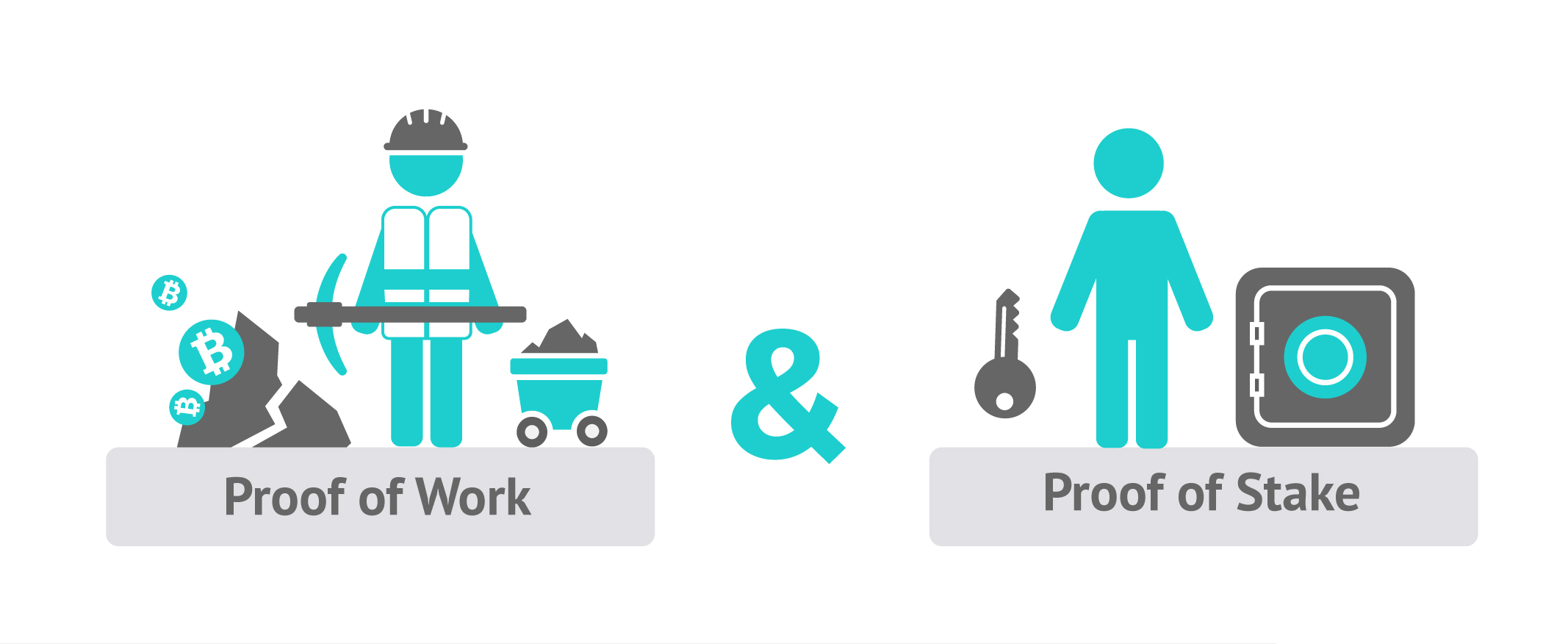
Cryptocurrencies use various timestamping schemes to “prove” the validity of transactions added to the blockchain ledger without the need for a trusted third party.
The first timestamping scheme invented was the proof-of-work scheme. The most widely used proof-of-work schemes are based on SHA-256 and scrypt.
Some other hashing algorithms that are used for proof-of-work include CryptoNight, Blake, SHA-3, and X11.
The proof-of-stake is a method of securing a cryptocurrency network and achieving distributed consensus by requesting users to show ownership of a certain amount of currency. It is different from proof-of-work systems that run difficult hashing algorithms to validate electronic transactions.
The scheme is largely dependent on the coin, and there’s currently no standard form of it. Some cryptocurrencies use a combined proof-of-work/proof-of-stake scheme.
Cryptocurrency Mining
In cryptocurrency networks, mining is a validation of transactions. For this effort, successful miners obtain new cryptocurrency as a reward.
The reward decreases transaction fees by creating a complementary incentive to contribute to the processing power of the network.
The rate of generating hashes, which validate any transaction, has been increased by the use of specialized machines such as FPGAs and ASICs running complex hashing algorithms like SHA-256 and Scrypt. This arms race for cheaper-yet-efficient machines has been on since the day the first cryptocurrency, bitcoin, was introduced in 2009.
With more people venturing into the world of virtual currency, generating hashes for this validation has become far more complex over the years, with miners having to invest large sums of money on employing multiple high-performance ASICs. Thus the value of the currency obtained for finding a hash often does not justify the amount of money spent on setting up the machines, the cooling facilities to overcome the enormous amount of heat they produce, and the electricity required to run them.
Some miners pool resources, sharing their processing power over a network to split the reward equally, according to the amount of work they contributed to the probability of finding a block. A “share” is awarded to members of the mining pool who present a valid partial proof-of-work.
As of February 2018, the Chinese Government halted trading of virtual currency, banned initial coin offerings and shut down mining. Some Chinese miners have since relocated to Canada. One company is operating data centres for mining operations at Canadian oil and gas field sites, due to low gas prices.
In June 2018, Hydro Quebec proposed to the provincial government to allocate 500 MW to crypto companies for mining. According to a February 2018 report from Fortune, Iceland has become a haven for cryptocurrency miners in part because of its cheap electricity. Prices are contained because nearly all of the country’s energy comes from renewable sources, prompting more mining companies to consider opening operations in Iceland. The region’s energy company says bitcoin mining is becoming so popular that the country will likely use more electricity to mine coins than power homes in 2018.
In October 2018 Russia becomes home to one of the largest legal mining operations in the world, located in Siberia.
In March 2018, a town in Upstate New York put an 18-month moratorium on all cryptocurrency mining in an effort to preserve natural resources and the “character and direction” of the city.

GPU demand is high for mining cryptocurrency: GPU price rise
An increase in cryptocurrency mining increased the demand for graphics cards (GPU) in 2017. Popular favourites of cryptocurrency miners such as Nvidia’s GTX 1060 and GTX 1070 graphics cards, as well as AMD’s RX 570 and RX 580 GPUs, doubled or tripled in price – or were out of stock.
A GTX 1070 Ti which was released at a price of $450 sold for as much as $1100. Another popular card GTX 1060’s 6 GB model was released at an MSRP of $250, sold for almost $500. RX 570 and RX 580 cards from AMD were out of stock for almost a year. Miners regularly buy up the entire stock of new GPU’s as soon as they are available.
Nvidia has asked retailers to do what they can when it comes to selling GPUs to gamers instead of miners. “Gamers come first for Nvidia,” said Boris Böhles, PR manager for Nvidia in the German region.
Cryptocurrency Wallets

An example paper printable bitcoin wallet consisting of one bitcoin address for receiving and the corresponding private key for spending
A cryptocurrency wallet stores the public and private “keys” or “addresses” which can be used to receive or spend the cryptocurrency. With the private key, it is possible to write in the public ledger, effectively spending the associated cryptocurrency. With the public key, it is possible for others to send currency to the wallet.
Blockchain Anonymity
Bitcoin is pseudonymous rather than anonymous in that the cryptocurrency within a wallet is not tied to people, but rather to one or more specific keys (or “addresses”).
Thereby, bitcoin owners are not identifiable, but all transactions are publicly available in the blockchain. Still, cryptocurrency exchanges are often required by law to collect the personal information of their users.
Additions such as Zerocoin have been suggested, which would allow for true anonymity.
In recent years, anonymizing technologies like zero-knowledge proofs and ring signatures have been employed in the cryptocurrencies Zcash and Monero, respectively. Cryptocurrency anonymizing implementations such as Cloakcoin, Dash, and PIVX use built-in mixing services, also known as tumblers.
The Fungibility of Cryptocurrency
Most cryptocurrency tokens are fungible and interchangeable. However, unique non-fungible tokens also exist. Such tokens can serve as assets in games like CryptoKitties.
The Economy of cryptocurrencies
Cryptocurrencies are used primarily outside existing banking and governmental institutions and are exchanged over the Internet.
Cryptocurrency Transaction fees
Transaction fees for cryptocurrency depend mainly on the supply of network capacity at the time, versus the demand from the currency holder for a faster transaction.
The currency holder can choose a specific transaction fee, while network entities process transactions in order of highest offered fee to lowest. Cryptocurrency exchanges can simplify the process for currency holders by offering priority alternatives and thereby determine which fee will likely cause the transaction to be processed in the requested time.
For ether, transaction fees differ by computational complexity, bandwidth use, and storage needs, while bitcoin transaction fees differ by transaction size and whether the transaction uses SegWit. In September 2018, the median transaction fee for ether corresponded to $0.017, while for bitcoin it corresponded to $0.55.
Cryptocurrency Exchanges
Cryptocurrency exchanges allow customers to trade cryptocurrencies for other assets, such as conventional fiat money, or to trade between different digital currencies.
Cryptocurrency Atomic swaps
Atomic swaps are a mechanism where one cryptocurrency can be exchanged directly for another cryptocurrency, without the need for a trusted third party such as an exchange.
Cryptocurrency ATMs
Jordan Kelley, the founder of Robocoin, launched the first bitcoin ATM in the United States on 20 February 2014. The kiosk installed in Austin, Texas is similar to bank ATMs but has scanners to read government-issued identification such as a driver’s license or a passport to confirm users’ identities.

Cryptocurrency Initial coin offerings (ICO)
An initial coin offering (ICO) is a controversial means of raising funds for a new cryptocurrency venture. An ICO may be used by startups with the intention of avoiding regulation.
However, securities regulators in many jurisdictions, including in the U.S., and Canada have indicated that if a coin or token is an “investment contract” (e.g., under the Howey test, i.e., an investment of money with a reasonable expectation of profit based significantly on the entrepreneurial or managerial efforts of others), it is a security and is subject to securities regulation.
In an ICO campaign, a percentage of the cryptocurrency (usually in the form of “tokens”) is sold to early backers of the project in exchange for legal tender or other cryptocurrencies, often bitcoin or ether.
According to PricewaterhouseCoopers, four of the 10 biggest proposed initial coin offerings have used Switzerland as a base, where they are frequently registered as non-profit foundations.
The Swiss regulatory agency FINMA stated that it would take a “balanced approach“ to ICO projects and would allow “legitimate innovators to navigate the regulatory landscape and so launch their projects in a way consistent with national laws protecting investors and the integrity of the financial system.”
In response to numerous requests by industry representatives, a legislative ICO working group began to issue legal guidelines in 2018, which are intended to remove uncertainty from cryptocurrency offerings and to establish sustainable business practices.

Cryptocurrency Legality
The legal status of cryptocurrencies varies substantially from country to country and is still undefined or changing in many of them.
While some countries have explicitly allowed their use and trade, others have banned or restricted it. According to the Library of Congress, an “absolute ban” on trading or using cryptocurrencies applies in eight countries: Algeria, Bolivia, Egypt, Iraq, Morocco, Nepal, Pakistan, and the United Arab Emirates. An “implicit ban” applies in another 15 countries, which include Bahrain, Bangladesh, China, Colombia, the Dominican Republic, Indonesia, Iran, Kuwait, Lesotho, Lithuania, Macau, Oman, Qatar, Saudi Arabia and Taiwan. In the United States and Canada, state and provincial securities regulators, coordinated through the North American Securities Administrators Association, are investigating “bitcoin scams” and ICOs in 40 jurisdictions.
Various government agencies, departments, and courts have classified bitcoin differently. China Central Bank banned the handling of bitcoins by financial institutions in China in early 2014.
In Russia, though cryptocurrencies are legal, it is illegal to actually purchase goods with any currency other than the Russian ruble. Regulations and bans that apply to bitcoin probably extend to similar cryptocurrency systems.
Cryptocurrencies are a potential tool to evade economic sanctions for example against Russia, Iran, or Venezuela.
In April 2018, Russian and Iranian economic representatives met to discuss how to bypass the global SWIFT system through decentralized blockchain technology. Russia also secretly supported Venezuela with the creation of the petro (El Petro), a national cryptocurrency initiated by the Maduro government to obtain valuable oil revenues by circumventing US sanctions.
In August 2018, the Bank of Thailand announced its plans to create its own cryptocurrency, the Central Bank Digital Currency (CBDC).

Cryptocurrency Advertising bans
Bitcoin and other cryptocurrency advertisements were temporarily banned on Facebook, Google, Twitter, Bing, Snapchat, LinkedIn and MailChimp. Chinese internet platforms Baidu, Tencent, and Weibo have also prohibited bitcoin advertisements. The Japanese platform Line and the Russian platform Yandex have similar prohibitions.
Cryptocurrency U.S. tax status
On 25 March 2014, the United States Internal Revenue Service (IRS) ruled that bitcoin will be treated as property for tax purposes. This means bitcoin will be subject to capital gains tax. In a paper published by researchers from Oxford and Warwick, it was shown that bitcoin has some characteristics more like the precious metals market than traditional currencies, hence in agreement with the IRS decision even if based on different reasons.
The legal concern of an unregulated global economy
As the popularity of and demand for online currencies has increased since the inception of bitcoin in 2009, so have concerns that such an unregulated person to person global economy that cryptocurrencies offer may become a threat to society. Concerns abound that altcoins may become tools for anonymous web criminals.
Cryptocurrency networks display a lack of regulation that has been criticized as enabling criminals who seek to evade taxes and launder money.
Transactions that occur through the use and exchange of these altcoins are independent of formal banking systems and therefore can make tax evasion simpler for individuals. Since charting taxable income is based upon what a recipient reports to the revenue service, it becomes extremely difficult to account for transactions made using existing cryptocurrencies, a mode of exchange that is complex and difficult to track.
Systems of anonymity that most cryptocurrencies offer can also serve as a simpler means to launder money. Rather than laundering money through an intricate net of financial actors and offshore bank accounts, laundering money through altcoins can be achieved through anonymous transactions.
Cryptocurrency: Loss, theft, and fraud
In February 2014 the world’s largest bitcoin exchange, Mt. Gox, declared bankruptcy. The company stated that it had lost nearly $473 million of their customers’ bitcoins likely due to theft. This was equivalent to approximately 750,000 bitcoins, or about 7% of all the bitcoins in existence. The price of a bitcoin fell from a high of about $1,160 in December to under $400 in February.
Two members of the Silk Road Task Force—a multi-agency federal task force that carried out the U.S. investigation of Silk Road—seized bitcoins for their own use in the course of the investigation. DEA agent Carl Mark Force IV, who attempted to extort Silk Road founder Ross Ulbricht (“Dread Pirate Roberts”), pleaded guilty to money laundering, obstruction of justice, and extortion under colour of official right, and was sentenced to 6.5 years in federal prison. U.S. Secret Service agent Shaun Bridges pleaded guilty to crimes relating to his diversion of $800,000 worth of bitcoins to his personal account during the investigation, and also separately pleaded guilty to money laundering in connection with another cryptocurrency theft; he was sentenced to nearly eight years in federal prison.
Homero Josh Garza, who founded the cryptocurrency startups GAW Miners and ZenMiner in 2014, acknowledged in a plea agreement that the companies were part of a pyramid scheme, and pleaded guilty to wire fraud in 2015.
The U.S. Securities and Exchange Commission separately brought a civil enforcement action against Garza, who was eventually ordered to pay a judgment of $9.1 million plus $700,000 in interest. The SEC’s complaint stated that Garza, through his companies, had fraudulently sold “investment contracts representing shares in the profits they claimed would be generated” from mining.
On 21 November 2017, the Tether cryptocurrency announced they were hacked, losing $31 million in USDT from their primary wallet. The company has ‘tagged’ the stolen currency, hoping to ‘lock’ them in the hacker’s wallet (making them unspendable). Tether indicates that it is building a new core for its primary wallet in response to the attack in order to prevent the stolen coins from being used.
In May 2018, Bitcoin Gold (and two other cryptocurrencies) were hit by a successful 51% hashing attack by an unknown actor, in which exchanges lost estimated $18m. In June 2018, Korean exchange Coinrail was hacked, losing US$37 million worth of altcoin. The fear surrounding the hack was blamed for a $42 billion cryptocurrency market selloff. On 9 July 2018, the exchange Bancor had $23.5 million in cryptocurrency stolen.
The French regulator Autorité des marchés financiers (AMF) lists 15 websites of companies that solicit investment in cryptocurrency without being authorised to do so in France.
Cryptocurrency Darknet markets
Cryptocurrency is also used in controversial settings in the form of online black markets, such as Silk Road. The original Silk Road was shut down in October 2013 and there have been two more versions in use since then.
In the year following the initial shutdown of Silk Road, the number of prominent dark markets increased from four to twelve, while the number of drug listings increased from 18,000 to 32,000.
Darknet markets present challenges in regard to legality. Bitcoins and other forms of cryptocurrency used in dark markets are not clearly or legally classified in almost all parts of the world. In the U.S., bitcoins are labelled as “virtual assets”.
This type of ambiguous classification puts pressure on law enforcement agencies around the world to adapt to the shifting drug trade of dark markets.

How are cryptocurrencies regarded as?
Cryptocurrencies have been compared to Ponzi schemes, pyramid schemes and economic bubbles, such as housing market bubbles. Howard Marks of Oaktree Capital Management stated in 2017 that digital currencies were “nothing but an unfounded fad (or perhaps even a pyramid scheme), based on a willingness to ascribe value to something that has little or none beyond what people will pay for it”, and compared them to the tulip mania (1637), South Sea Bubble (1720), and dot-com bubble (1999).
While cryptocurrencies are digital currencies that are managed through advanced encryption techniques, many governments have taken a cautious approach toward them, fearing their lack of central control and the effects they could have on financial security.
Regulators in several countries have warned against cryptocurrency and some have taken concrete regulatory measures to dissuade users. Additionally, many banks do not offer services for cryptocurrencies and can refuse to offer services to virtual-currency companies.
Gareth Murphy, a senior central banking officer has stated: “widespread use [of cryptocurrency] would also make it more difficult for statistical agencies to gather data on economic activity, which are used by governments to steer the economy”. He cautioned that virtual currencies pose a new challenge to central banks’ control over the important functions of monetary and exchange rate policy.
While traditional financial products have strong consumer protections in place, there is no intermediary with the power to limit consumer losses if bitcoins are lost or stolen.
One of the features cryptocurrency lacks in comparison to credit cards, for example, is consumer protection against fraud, such as chargebacks.
An enormous amount of energy goes into proof-of-work cryptocurrency mining, although cryptocurrency proponents claim it is important to compare it to the consumption of the traditional financial system.
There are also purely technical elements to consider. For example, technological advancement in cryptocurrencies such as bitcoin results in high up-front costs to miners in the form of specialized hardware and software.
Cryptocurrency transactions are normally irreversible after a number of blocks confirm the transaction. Additionally, cryptocurrency can be permanently lost from local storage due to malware or data loss. This can also happen through the destruction of the physical media, effectively removing lost cryptocurrencies forever from their markets.
The cryptocurrency community refers to pre-mining, hidden launches, ICO or extreme rewards for the altcoin founders as a deceptive practice. It can also be used as an inherent part of a cryptocurrency’s design. Pre-mining means the currency is generated by the currency’s founders prior to being released to the public.
Paul Krugman, Nobel Memorial Prize in Economic Sciences winner does not like bitcoin, has repeated numerous times that it is a bubble that will not last and links it to Tulip mania. American business magnate Warren Buffett thinks that cryptocurrency will come to a bad ending.
In October 2017, BlackRock CEO Laurence D. Fink called bitcoin an ‘index of money laundering’. “Bitcoin just shows you how much demand for money laundering there is in the world,” he said.
Source wikipedia.org